How Okta Was Hacked and What That Means for the Stock
Table of contents

Some alarming news this past week on Thirsty Thursday. No, we’re not talking about that hard-hitting HuffPo piece exploring Amy Schumer’s secret hair pulling disorder, something we suspect stems from her inability to do standup comedy without mentioning her private parts. The news was much more dire than that, at least for shareholders of Okta (OKTA), a company we last looked at in a piece titled Okta Stock Forecast: Growth with a Chance of Dominance.
When a cybersecurity company like Okta is openly critical about how other firms protect themselves, and then they get compromised themselves, it will raise some eyebrows. Below we have an Okta executive talking smack about one of their largest competitors – Microsoft – just weeks before his own firm aired some major dirty laundry.

We caught wind of this issue on March 22nd when several screenshots were published online taken from a computer used by one of Okta’s third-party customer support engineers. On the same day, the CEO of Okta posts on (checks notes) Twitter about how the firm “believes” that the screenshots shared related to a known breach and that there is “no evidence of ongoing malicious activity.” His statement casts seeds of doubt and fails to address what might have happened between January 2022 and March 2022:
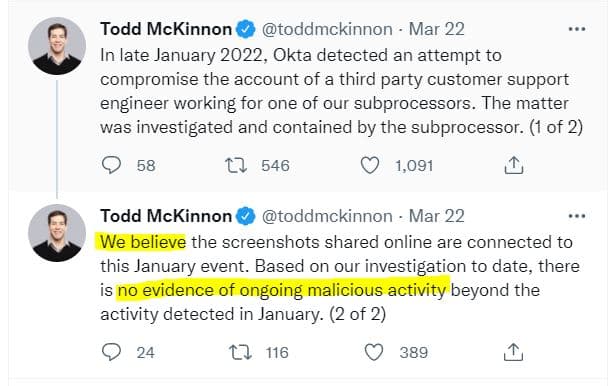
A CEO should never post things on Twitter with such little conviction. Elon Musk can post on Twitter because he makes emphatic statements that don’t mince words. That’s what BSDs do. Okta’s legal team likely vetted this message which tries to instill trust while avoiding culpability. The sharks smelled blood, and armchair Twitter cybersecurity experts are coming out of the woodwork to condemn the company in the strongest possible terms. Maybe we should understand what happened before casting judgment.
A Timeline of Events
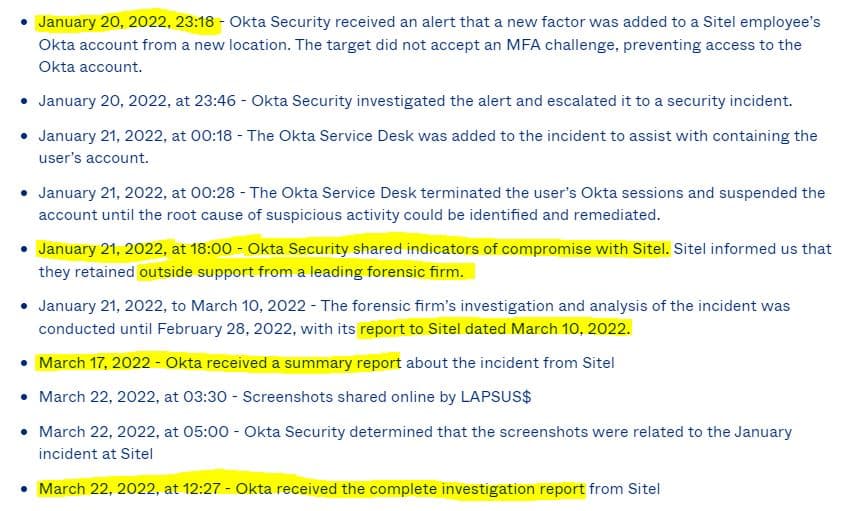
Twenty four hours after compromising screenshots started appearing on Twitter, Okta’s Chief Security Officer published their investigation of the event – Okta’s Investigation of the January 2022 Compromise. Simply put, there was a five-day window of time between January 16-21, 2022, where an attacker had access to the laptop of a support engineer who worked for an Okta vendor named Sitel – a Miami-based leading provider of business process outsourcing (BPO) services related to customer care. The timeline of the event shows what typically happens when multiple firms pass the buck – there is absolutely no sense of urgency. Sensitive businesses should never outsource operations to third parties because this is what happens:
Let’s start with the access window and user permissions for the role that was compromised – a third-party customer support engineer.
The Actual Intrusion
The problem started when Okta’s security team was notified of a suspicious authentication attempt for an account. Within 70 minutes of a potential issue being identified, Okta had suspended the account and the perpetrator lost their access. That was on January 21, 2022. Unfortunately, the compromise began on January 16th, 2022. During those five days, the perpetrator had limited permissions that third-party support engineers are granted including access to:
- Okta’s instances of Jira, Slack, Splunk, RingCentral, and support tickets through Salesforce.
- An internally-built application called SuperUser used to perform basic management functions for Okta customers
Third-party vendors should never be provided access to internal company tools. If they are, it’s usually through a narrowly controlled set of privileges. For example, here are some of the things that the compromised support engineer account could not do:
- Create or delete users.
- Download customer databases
- Access source code repositories.
- Obtain account passwords (though they can help facilitate their reset)
When evaluating what actions the perpetrators took, Okta assumed a blast radius that included all activity coming from Sitel during the access window by analyzing 125,000 activity logs. In a worst-case scenario, 365 client accounts (2.5% of the total) could have been affected by the breach, but it’s hard to see what havoc could be wreaked with read-only access to internal IT support tools. What clients may be more concerned about is assurance that this event won’t happen again. Here’s how the perps were able to gain access in the first place.
Remote Desktop Protocol
There’s a clever scam going around in the USA right now for the many elderly people who maintain a landline. You’ll get a call from your Internet service provider saying that there’s a problem with the Internet connection. Since our entire lives revolve around accessing the Internet, this is seen as a concern by most who won’t suspect much as the perpetrator knows basic information – their address, their age, other people living in the house, even their account number perhaps. Once trust has been developed, the mark is convinced to approve remote desktop connectivity through TeamViewer or Remote Desktop Services (RDS). The latter is a purposefully built back door protocol built by Microsoft that allows someone to control a machine remotely while another person is logged in.
That’s the same thing that happened here, except the mark was probably paid a whole bunch of money for looking in the other direction. The perpetrator was able to remotely control a machine using the support engineer’s credentials, something that was best described by the CSO as follows:
The scenario here is analogous to walking away from your computer at a coffee shop, whereby a stranger has (virtually in this case) sat down at your machine and is using the mouse and keyboard. So while the attacker never gained access to the Okta service via account takeover, a machine that was logged into Okta was compromised and they were able to obtain screenshots and control the machine through the RDP session.
Credit: Okta CSO, David Bradbury
Ironically, this further underscores the importance of a “zero trust” solution, precisely the kind that Okta offers. You can never assume that the person on the other end of the connection is who they say they are. It was a Sitel device being used by the support engineer, so we’ll never get to know the dirty details. What we can do is try and understand the motivations of those who broke through Okta’s iron curtain of security by exploiting labor resources under someone else’s remit.
Profiling the Perpetrator
The group behind the attack, LAPSUS$, is a relatively new cybercrime group that specializes in stealing data from big companies and threatening to publish it unless a ransom demand is paid. They had already tangled with Microsoft, NVIDIA, and Samsung. Reports say they’re a bunch of clever teenagers who exploit the largest vulnerability for any organization – humans – and then try and extort money from the companies they target. Apparently, they weren’t very careful covering their tracks, and London police have already arrested seven individuals aged 16 to 21 with the mastermind being a 16-year-old Oxford teenager with autism who has already amassed $14 million in bitcoin through data extortion activities. (All you Web 3.0 zealots take note; we wouldn’t be dealing with teenage data extortion gangs were it not for the emergence of cryptocurrencies and the freedom and autonomy of decentralized finance.)
An excellent article by Krebs on Security talks about how LAPSUS$ operated. They use the oldest trick – social engineering – accompanied by some healthy cash rewards which were no doubt paid in cryptocurrency:
For a fee, the willing accomplice must provide their credentials and approve the MFA prompt or have the user install AnyDesk or other remote management software on a corporate workstation allowing the actor to take control of an authenticated system.
MIcrosoft
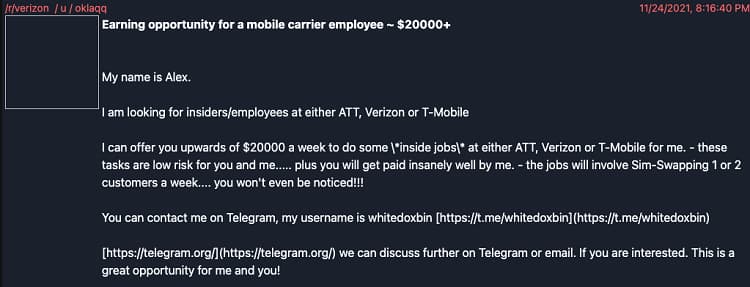
Multi-factor authentication (MFA) is a secure way to ensure the person authenticating is who they say they are. When you login into your bank account and they email you a numeric code to enter, that’s MFA. In this case, LAPSUS$ was looking for ways to bypass this second level of authentication and they were willing to pay handsomely for that. Below is an actual ad from the group trying to solicit employees willing to commit crimes for money.
We’re going to address the elephant in the room. Sure, $20,000 a week is a lot of money for anyone, but when you make $10,000 a year working in a Manila call center, earning eight years’ worth of salary for one month of work is going to sound pretty compelling. It’s precisely the same reason Russian engineers in Samara graduate from university and go to the dark side. The rewards are just too tempting. And if you think emerging market justice systems are capable of punishing the perpetrators when they’re caught, maybe you need to spend some time in these places and see just how easily justice can be swayed with the almighty dollar.
Going back to the issue timeline, hours after the compromised account was suspended, Okta informed their vendor of the security event. Sitel then “retained outside support from a leading forensic firm.” That investigation lasted a month and a week, ending on February 28th. Ten days later (March 10th), the forensics firm provided Sitel a report. A week later (March 17th), Sitel provided a “summary report” to Okta. The data extortion group then started posting screenshots five days later, and on that same day Sitel suddenly procured the “complete report” for Okta’s investigation. The entire timeline shows no sense of urgency from anyone involved and we can only hope Okta has already made the decision to move all support functions in-house.
A Buying Opportunity for Okta Stock?
We analyze unexpected events like this to determine how they affect our fundamental investment thesis. We have to assume that Okta is being transparent at this point in time. The alternative is that we don’t trust management, in which case we should exit our position immediately. Investing in a company means we assume the management team is fulfilling their fiduciary responsibility. Based on the information we’ve been provided so far, we can attempt to answer the below questions (our comments in italics):
- Could this have been prevented? Yes. But as the old saying goes, there are two types of companies in the world: those who have been hacked and those who will be hacked. Being hacked wasn’t the problem, it was how Okta handled it.
- What’s the root cause of the incident? Outsourcing customer support tasks to third parties. You always keep that stuff in-house and carefully consider your emerging market labor exposure.
- What’s the worst that could have happened? Okta knows everything that support engineer did during their existence at the firm. They also expanded scope to include all Sitel activities. Any reasonably capable forensics team could figure out quickly what actually transpired.
- The effectiveness of their own solution – where they eating their own dog food when this happened? A proper zero-trust solution of the type Okta builds would have prevented this breach. Because this happened on a device controlled and operated by a third party, we will never have any insights into how badly Sitel dropped the ball on security.
- The ability of the company to handle a crisis internally – Clearly lacking. The Okta CSO came from Symantec a few years ago so its likely heads are rolling internally right now as he now goes about finding where all the bodies are buried.
- Will clients forgive and forget? C.K Louis sold out the Mercedes Benz arena in Berlin last week after supposedly being canceled. Yes, they’ll make a big fuss and act all outraged, and 365 clients will use this as a negotiation tactic come renewal time, but people have short attention spans and they’ll forget soon enough.
Okta is a $20 billion firm with 14,600 clients. Just 2.5% of their user base might have been affected so they’ll need to fight those fires. One year from now, the 97.5% that weren’t affected will have forgotten about the whole thing. The most important conversations need to happen with the 2,444 customers who pay more than $100,000 a month.

It all comes back to trusting that management was a) capable enough to correctly gauge impact of the security event and b) isn’t hiding anything. A group of teenagers seeking money and clout who weren’t smart enough to cover their tracks probably didn’t have too many sinister motives. One can only hope.
Conclusion
Hacking a cybersecurity company is the ultimate score for someone looking to build cred. Okta made a number of mistakes that created the dilemma they find themselves in. Allowing third parties access to internal systems is the root cause of the problem at a strategic level. At a tactical level, there seems to be no sense of urgency around achieving resolutions for security issues. They’ll likely fight fires over the next few months and spend loads of time assuring key customers this issue doesn’t represent any systemic risk to their operation. In the meantime, there’s no reason to believe they won’t recover from this temporary setback.
Sign up to our newsletter to get more of our great research delivered straight to your inbox!
Nanalyze Weekly includes useful insights written by our team of underpaid MBAs, research on new disruptive technology stocks flying under the radar, and summaries of our recent research. Always 100% free.















How come do you consider Okta a ‘dominant leader’? Palo Alto’s revenues are 5 times higher and Fortinet’s more then 3 times?
Do they compete on the same cybersecurity space?
Palo Alto looks cheaper too.
Thanks
Best
Please see the Magic Quadrant referenced in the following article: https://nanalyze.com/2021/11/okta-stock-forecast-growth/
The term cybersecurity encompasses a broad set of functional areas. Okta operates in customer identity and access management with a focus on “zero trust” which is where the industry appears to be heading. Trust nobody, even those already authenticated within your network. Here’s a piece we did looking at the largest cybersecurity stocks, Palo Alto and Fortinet being two of them: https://nanalyze.com/2021/04/biggest-cybersecurity-stocks-best/
Hmm…., very cynical to conclude that business will go on just fine, but you are very probably right. Companies seem to purchase this “insurance” of “zero trust ID mgmt” even so they know it does not exist / works as “advertised” & Okta just proved that what they sell does not work in their own house. Maybe Okta’s business is really just charging a premium for shifting liability; but then is it worth investing in (beyond a volatility trade)? Eventually the “Potemkin village” will crumble.
Thanks for the comment Axel. Always love to hear what other people think on thorny issues like this.
We’re hoping Okta does offers a value proposition that companies find compelling otherwise they wouldn’t have achieved the rapid revenue growth we see today. The concept of “zero trust” is very important because ultimately you can never be sure who is on the other side of a keyboard. This domain is actually quite fascinating and they’re using some very clever ways to monitor – during sessions – that the same person is at the keyboard at all times. (We all wake up our mouse in a different manner.) This started in online banking and it’s now moving on to other domains. As for this event, we have no idea what security was in place on the machine that was compromised which was owned and used by Sitel. We didn’t see this as a case of the solution not working as advertised given that we don’t know the extent to which it was being used by Sitel. If Okta would have kept this support function in house we wouldn’t be having this conversation.